Learn How To Hack Websites , Mysql Injection Tutorial
SQL Injection in MySQL Databases
SQL
Injection attacks are code injections that exploit the database layer
of the application. This is most commonly the MySQL database, but there
are techniques to
...
Read more »
|
SQL injection is a very popular and easy hack
technique of WEB 2.0 application and by using following tools you can
your self try you’re Luck. I will write further tutorials to use these
things.
Checking
for SQL Injection vulnerabilities involves auditing your web
applications and the best way to do it is by using automated SQL
Injection Scanners. I’ve compiled a list of free SQL Injection Scanners I
belie
...
Read more »
|
1. SQLi Helper 2.7 by reiluke
Very useful tool. Just type vun website link and hit inject.
Download link:
|
Contents
1A: Understanding SQL Injection
1B: Tricks & Tools
1C: Requirements
------
2A: Searching for Targets
2B: Testing Targets for Vulnerabilities
2C: Finding Columns
2D: Finding Vulnerable Columns
...
Read more »
|
Description: Havij
is an automated SQL Injection tool that helps penetration testers to
find and exploit SQL Injection vulnerabilities on a web page. It
can take advantage of a vulnerable web application. By using this
software user can perform back-end database fingerprint, retrieve DBMS
users and pass
...
Read more »
|

The following is a list of Google Dorks for SQLi Injection:
inurl:index.php?id=
inurl:trainers.php?id=
inurl:buy.php?category=
inurl:article.php?ID=
inurl:lay_old.php?id=
inurl:declaration_more.php?decl_id=
inurl:ageid=
inurl:games.php?id=
inurl:age.php?file=
inurl:newsDetail.ph
...
Read more »
|
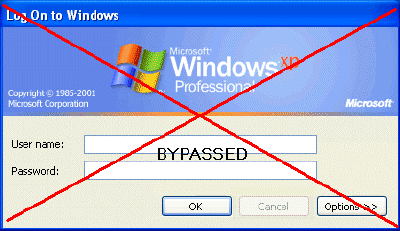
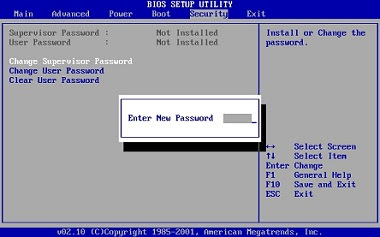
There is a far better way to get into Windows XP. It is easy and it does
not reset
...
Read more »
|
Do you have any private stuff that you would to
hide from your friends and relatives? Would you want it to be Invisible
so that it remains unnoticed by the normal users? But there are software
which can display all the folders that are present on the Disk. So What
if you can even password
protect your folder? I guess having your private folder password
protected as well as invisible should
...
Read more »
|
I don’t want to type a whole book. So just goto www.unblockall.net . Download the Soft and Enjoy!!!.
Enough Work for today I m going to sleep ; ) LOL |
Sometimes when you are executing some program an
error comes saying that your xxx file is corrupted so we can not run
your program and your whole work is left pending due to that error. Now
this problem will not arise because I will show you how to fix these
corrupted files.
Required:
1. Windows XP operating system
|
Did know that you could clone your current Hard
Drive without having to by extra software? Maybe you didn’t know that
all that you needed, was already set up on your current system? Well, it
is… and if you follow this tut, you shouldn’t have much of a problem.
Make
sure that you have a Master and a Slave setup on your system. The Slave
drive, in this case, is where all the data on the Master is going to go
...
Read more »
|
Leaving your computer in a hurry but you don’t
want to log off? You can double-click a shortcut on your desktop to
quickly lock the keyboard and display without using CTRL+ALT+DEL or a screen saver.
Here the steps to create a shortcut on your desktop to lock your computer:
|
This is the Collection of Best Windows Hacking Tools:
1. Cain & Abel – Cain & Abel
is a password recovery tool for the Microsoft Windows Operating System.
It allows easy recovery of various kind of passwords by sniffing the
network, cracking encrypted passwords using Dictionary, Brute-Force and
Cryptanalysis attacks, recording VoIP conversations, decoding s
...
Read more »
|
I
have seen many different attempts at creating a USB hacking tool. The
switchblade and hacksaw were okay, but they would set off many alarms
deeming it useless, so I propose something different.
This uses
(3) simple batch files, Go.bat, injector.bat, and sysinfo.bat. Save all
three of these
...
Read more »
|
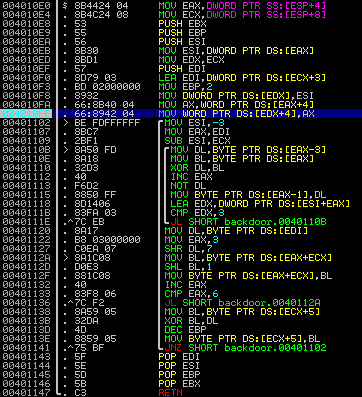
There is a general misconception about security
today. Most people would love to believe that their firewalls are
completely capable to protect them from anything indecent. The sad part,
they could not be more wrong. Hungry Hacker aim to prove it with three
separate programs that can compromise the security of computers. You
have the opportunity to say "What’s a backdoor?” Yes, these programs
were created in 1990, but still pose a real threat today. It is the
first
...
Read more »
|
Well this is the question in every bodies mind that how can we hack a
email account or How do others do it. When I started reading about
Hacking I also search about this question and sea
...
Read more »
|
 Hi
friends, the most interesting part of the hacking is spying. Today i
am going to introduce to the C++ Spyware code at geniussoftdl. It is going to be very
fun. You can install this spyware in your college/school or in your
friend system, and get their username and passwords. This is very
simple hacking t
...
Read more » Hi
friends, the most interesting part of the hacking is spying. Today i
am going to introduce to the C++ Spyware code at geniussoftdl. It is going to be very
fun. You can install this spyware in your college/school or in your
friend system, and get their username and passwords. This is very
simple hacking t
...
Read more »
|
Top 15 Security/Hacking Tools & Utilities
1. Nmap I think everyone has heard of this one, recently evolved into the 4.x series. Nmap
(”Network Mapper”) is a free open source utility for
network exploration or security auditing. It was designed
...
Read more »
|
It is easy and it does not reset the password. Hack into a computer running Windows XP
without changing the password and find out a
...
Read more »
|
I will cover 4 methods over here:
1. Facebook Phishing
...
Read more »
|
Recently a new firefox addon Firesheep have been a cause of thousands of
...
Read more »
|
|




 <
<


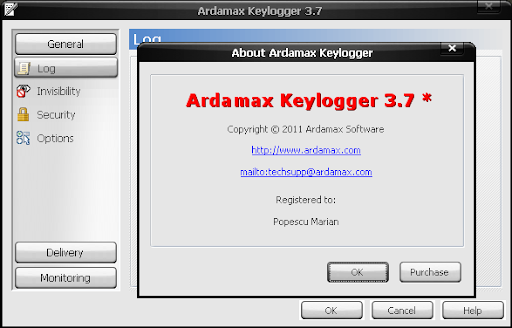


 Hi
friends, the most interesting part of the hacking is spying. Today i
am going to introduce to the C++ Spyware code at geniussoftdl. It is going to be very
fun. You can install this spyware in your college/school or in your
friend system, and get their username and passwords. This is very
simple hacking t
Hi
friends, the most interesting part of the hacking is spying. Today i
am going to introduce to the C++ Spyware code at geniussoftdl. It is going to be very
fun. You can install this spyware in your college/school or in your
friend system, and get their username and passwords. This is very
simple hacking t




