| Main » Articles » All About Hacking » Malware |
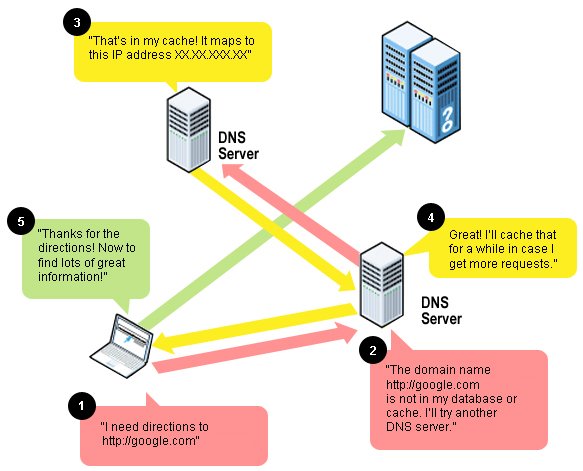
DNS Changer is a trojan horse that has been reported to have infected around 4 million computers all over the world by now. The trojan is so powerful that it can blacken out the complete internet. The trojan works out by altering the DNS settings of the victim’s ISP, thereby completely messing up the domain and IP mapping, redirecting the genuine URLs to open fraudulent and malicious websites, leaving behind the victim wondering. The malware is still persistent and still infects around 330,000 computers all over the world. This trojan is said to have illegally earned the fraud money sum of around $14 million from the time it was first discovered in 2007, though the seven people involved with this trojan have been busted by the FBI last November. What exactly is a Domain Name Server (DNS) ? Suppose that we enter a particular URL, say http://google.com, the request passes on to the associated DNS servers to resolve this domain name to its corresponding IP address. There is a chain of requests to the DNS servers until and unless the domain name is resolved, that completely depends on my ISP, the DNS servers it provides. Following is the image that shows it all:
By default, the ISP automatically assigns us the DNS servers, though we know that some computer geeks prefer entering them manually. A brief insight into DHCP DHCP stands for Dynamic Host Configuration Protocol. I will be very straightforward and precise in explaining you. The moment you connect yourselves to the internet, the DHCP server automatically assigns the IP address to your computer, default gateway, subnet mask, the DNS server and other IP configuration parameters. Actually, these parameters are managed by the DHCP servers. DHCP servers manage the pool of IP addresses too, such that the next moment when client disconnects from the internet, the previously assigned IP address gets added back to the pool. I hope you more or less got the basic idea. How DNS Changer works? DNS Changer is a deadly trojan, also referred to be the variants of the Zlob Family. Basically, they try penetrating into a network running DHCP servers for dynamic configuration and getting access to the gateway/router. They bruteforce the device login with common username and passwords, and once successful, enter the configuration setting of the devices and change the ISP’s genuine DNS servers to fraudulent ones, which are operated remotely by the criminals. Once these device settings get screwed, the impact can be seen in all the terminals/computers attached to it, though they haven’t been actually infected by the trojan. The malicious/rogue DNS servers redirect the genuine URLs to open fraudulent and malicious websites. FBI are said to have uncovered the network of those malicious DNS servers operating behind the scenes, but they have been stopped from disabling them, since there still are the victims who rely on these malicious DNS servers for the DNS services. FBI has temporarily arranged the clean DNS servers for these infected victims providing them with the time space to get themselves out this infection and get it fixed, instead of explicitly shutting down the rogue DNS servers immediately. These clean DNS servers are most commonly referred as the Ghost Click servers. | |
| Views: 1022 | Rating: 3.5/2 |
| Total comments: 0 | |