Main » 2011 » February » 2 » How email works tutorial
11:03 PM How email works tutorial | |
Hello friends, today i am going to explain you how an email address works. We will proceed step by step How email works tutorial. Why did we need to understand the working of emails , just for curiosity! No really don't.
The real motive behind learning How email works is that if we know things that how they works then we can easily prevent our self from being hacked or attacked by hackers or malwares. So friends keep reading the article...
From the general user point of view, the working of emails looks quite simple. You select the address of the person to whom you want to send the email, compose your message and click 'Send'.
But in reality the working of emails is quite complicated. Before proceeding further i will introduce some terms that i will use frequently so i prefer to define them at start.
1. Mail User Agent (MUA) : The MUA is the application the sender(who composes mail) uses to compose and read email, such as Eudora, Outlook, Thunderbird, etc.
2. Mail Delivery Agent (MDA): A mail delivery agent or message delivery agent (MDA) is a computer software component that is responsible for the delivery of e-mail messages to a local recipient's mailbox.
3. Mail Transfer Agent (MTA): A message transfer agent or mail transfer agent (MTA) or mail relay is software that transfers electronic mail messages from one computer to another using a client-server application architecture.
4. Domain Name System (DNS):In simpler words, a domain name system (DNS) translates the domain name to IP addresses.
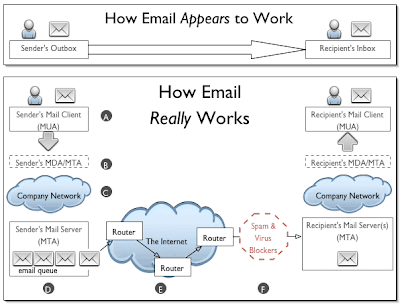
STEPWISE WORKING OF EMAILS:
Step A: Sender creates and sends an emailThe originating sender creates an email in their Mail User Agent (MUA) and clicks 'Send'. The MUA is the application the originating sender uses to compose and read email, such as Eudora, Outlook, Thunderbird, etc.
Step B: Sender's MDA/MTA routes the emailThe sender's MUA transfers the email to a Mail Delivery Agent (MDA). Frequently, the sender's MTA also handles the responsibilities of an MDA. Several of the most common MTAs do this, including send-mail and qmail (which Gmail uses). The MDA/MTA accepts the email, then routes it to local mailboxes or forwards it if it isn't locally addressed. In our diagram, an MDA forwards the email to an MTA and it enters the first of a series of "network clouds," labeled as a "Company Network" cloud.
Step C: Network cloudAn email can encounter a network cloud(means Internet) within a large company or ISP( Internet Service Provider), or the largest network cloud in existence: the Internet. The network cloud may encompass a multitude of mail servers, DNS servers, routers, lions, tigers, bears (wolves!) and other devices and services too numerous to mention. These are prone to be slow when processing an unusually heavy load, temporarily unable to receive an email when taken down for maintenance, and sometimes may not have identified themselves properly to the Internet through the Domain Name System (DNS) so that other MTAs in the network cloud are unable to deliver mail as addressed. These devices may be protected by firewalls, spam filters and malware detection software that may bounce or even delete an email. When an email is deleted by this kind of software, it tends to fail silently, so the sender is given no information about where or when the delivery failure occurred. Email service providers and other companies that process a large volume of email often have their own, private network clouds. These organizations commonly have multiple mail servers, and route all email through a central gateway server (i.e., mail hub) that redistributes mail to whichever MTA is available. Email on these secondary MTAs must usually wait for the primary MTA (i.e., the designated host for that domain) to become available, at which time the secondary mail server will transfer its messages to the primary MTA.
Step D: Email queueThe email in the diagram is addressed to someone at another company, so it enters an email queue with other outgoing email messages. If there is a high volume of mail in the queue—either because there are many messages or the messages are unusually large, or both—the message will be delayed in the queue until the MTA processes the messages ahead of it. Step E: MTA to MTA transferAs the email clears the queue, it enters the Internet network cloud, where it is routed along a host-to-host chain of servers. Each MTA in the Internet network cloud needs to "stop and ask directions" from the Domain Name System (DNS) in order to identify the next MTA in the delivery chain. The exact route depends partly on server availability and mostly on which MTA can be found to accept email for the domain specified in the address. Most email takes a path that is dependent on server availability, so a pair of messages originating from the same host and addressed to the same receiving host could take different paths. These days, it's mostly spammers that specify any part of the path, deliberately routing their message through a series of relay servers in an attempt to obscure the true origin of the message. To find the recipient's IP address and mailbox, the MTA must drill down through the Domain Name System (DNS), which consists of a set of servers distributed across the Internet. Beginning with the root nameservers at the top-level domain (.tld), then nameservers that handle requests for domains within that .tld, and eventually to nameservers that know about the local domain. Step F: Firewalls, spam and virus filtersThe transfer process described in the last step is somewhat simplified. An email may be transferred to more than one MTA within a network cloud and is likely to be passed to at least one firewall before it reaches it's destination. An email encountering a firewall may be tested by spam and virus filters before it is allowed to pass inside the firewall. These filters test to see if the message qualifies as spam or malware. If the message contains malware, the file is usually quarantined and the sender is notified. If the message is identified as spam, it will probably be deleted without notifying the sender. Spam is difficult to detect because it can assume so many different forms, so spam filters test on a broad set of criteria and tend to misclassified a significant number of messages as spam, particularly messages from mailing lists. When an email from a list or other automated source seems to have vanished somewhere in the network cloud, the culprit is usually a spam filter at the receiver's ISP or company. This explained in greater detail in Virus Scanning and Spam Blocking.
For More About Emails Working keeps reading. In my Next Posts I will explain How to trace any email address that from where it has been sent and who sent it and whats is computer name and much more...
If you Have Any Queries Post your Comments!
| |
|
| |
| Total comments: 0 | |